<Updated 11th July 2019>
Since we started to help customers of all sizes to deploy cloud technologies, we have developed many frameworks which all evolved in parallel over time. You may have heard about: Cloud Adoption Framework, Cloud Operations Model, Entreprise Cloud Strategy, Entreprise Scaffolding and maybe a couple more.
The CAF is dead, long live the CAF!
A couple of weeks ago, we published a new version of CAF – Cloud Adoption Framework for Azure, which consolidates all of our engineering and field best practices, as well as patterns that we’ve seen from big entreprises going to the cloud.
CAF has now five main sections which guide you throughout the whole circle:
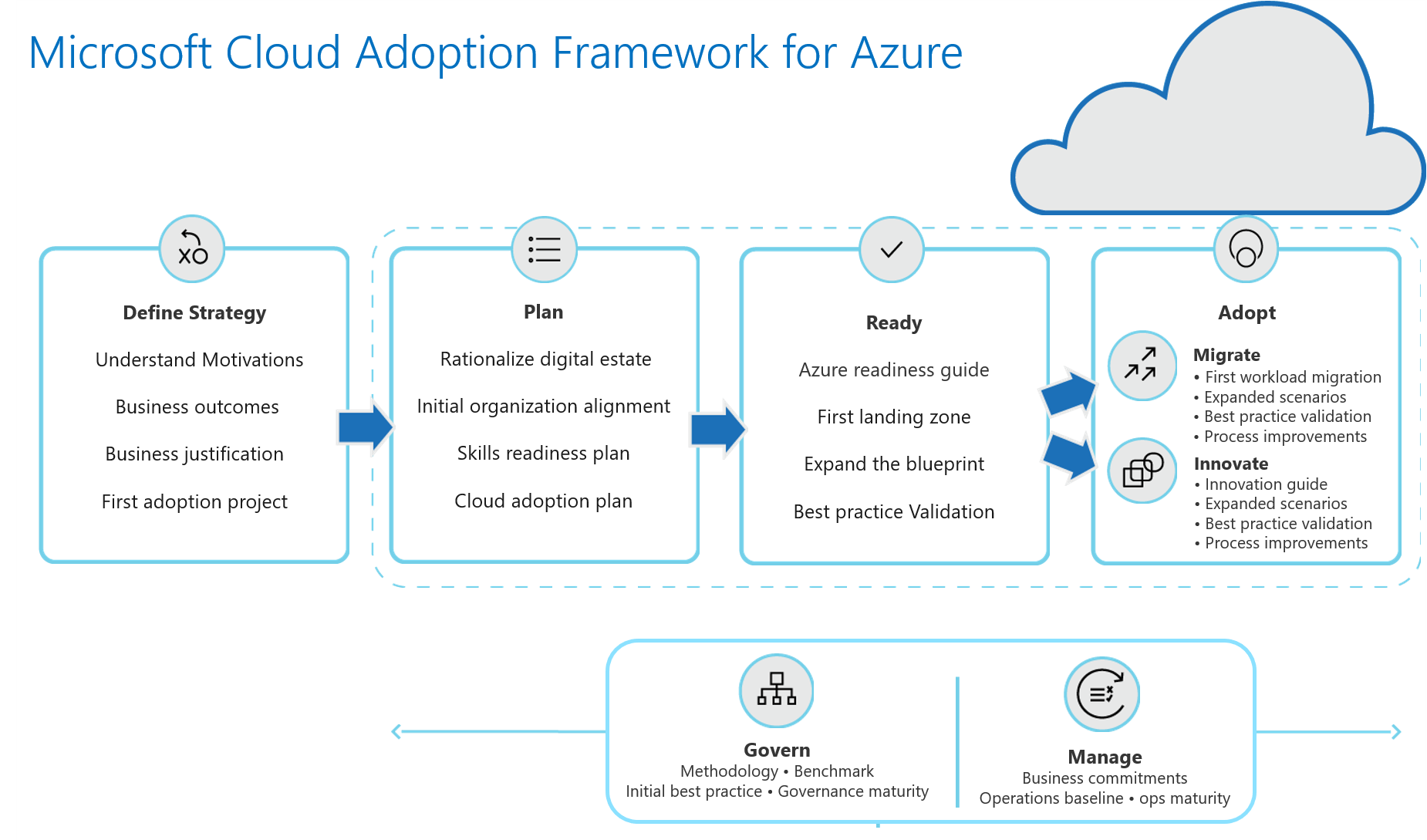
- Plan
- Ready
- Migrate
- Manage
- Govern
This model is very realistic and field inspired, including some discussions around adoption with one or more cloud providers.
Governance
One of the most intimidating aspects of cloud adoption is the governance: how to manage new risks that are involved with cloud deployments and how to accompany that with entreprise processes and policies (and how does it remain current).
It is of course an iterative process that will evolve as you add new services into your environment: from dev/test to prod, and from legacy 3-tiers application to a brand new cloud-native application.
We distinguish 5 disciplines in governance:
- Cost management
- Security baseline
- Resource consistency
- Identity baseline
- Deployment Acceleration
But the difficulty is the first step: how do I get a minimal viable product (MVP) for my first cloud deployment?
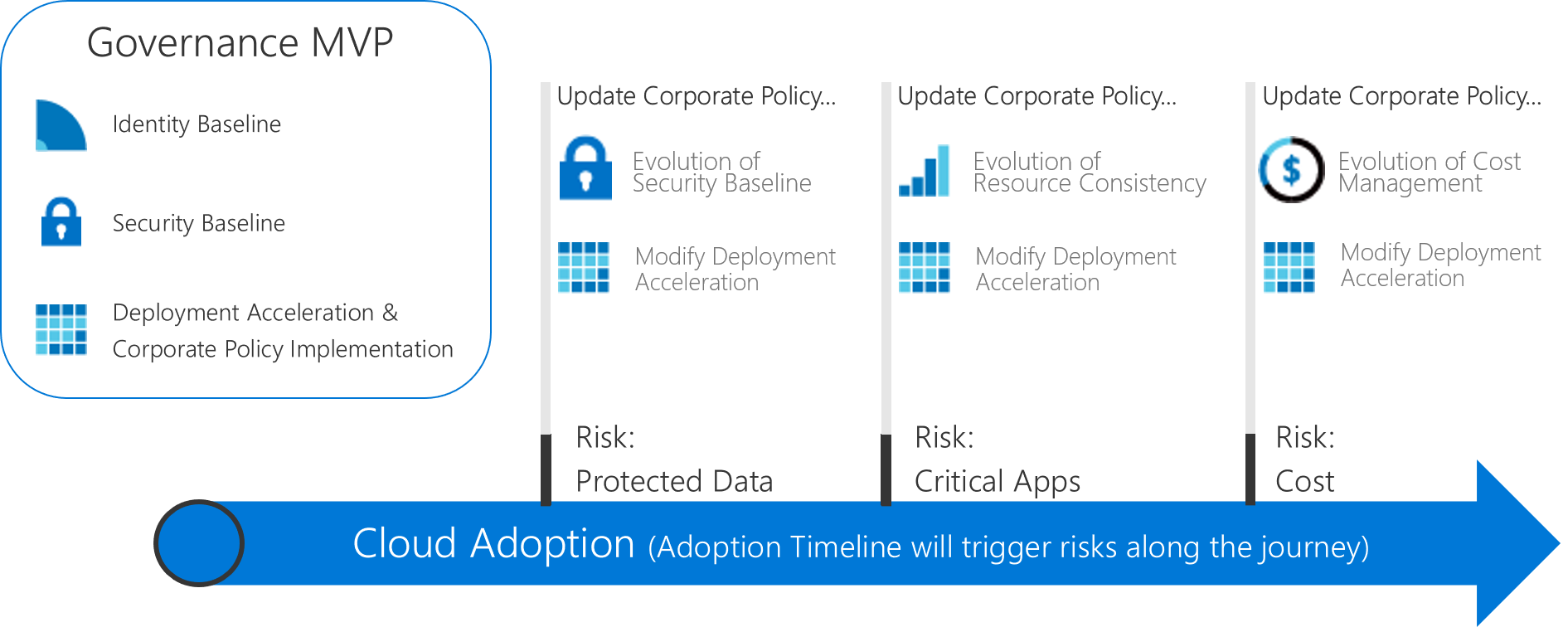
Actions: In order to avoid you the blank page syndrome, we have prepared you some actions:
- Determine your immediate objectives with cloud, and the readiness of your organization. Cloud Assessment Tool: https://aka.ms/CAF/gov/assess
- Establish your governance MVP:
- Small to Medium Entreprises
- Large Entreprises
For all those journey we document a minimum viable product across the five disciplines, we explain the design decisions we took for you, the discussion points and alternative design considerations.
When we define governance, we also think about compliance to the rules, and automatic remediation methods for it: this is called Azure Policy.
Along the way, if you are going for ongoing compliance, why not going to continuous integration and continuous deployment for your infrastructure?
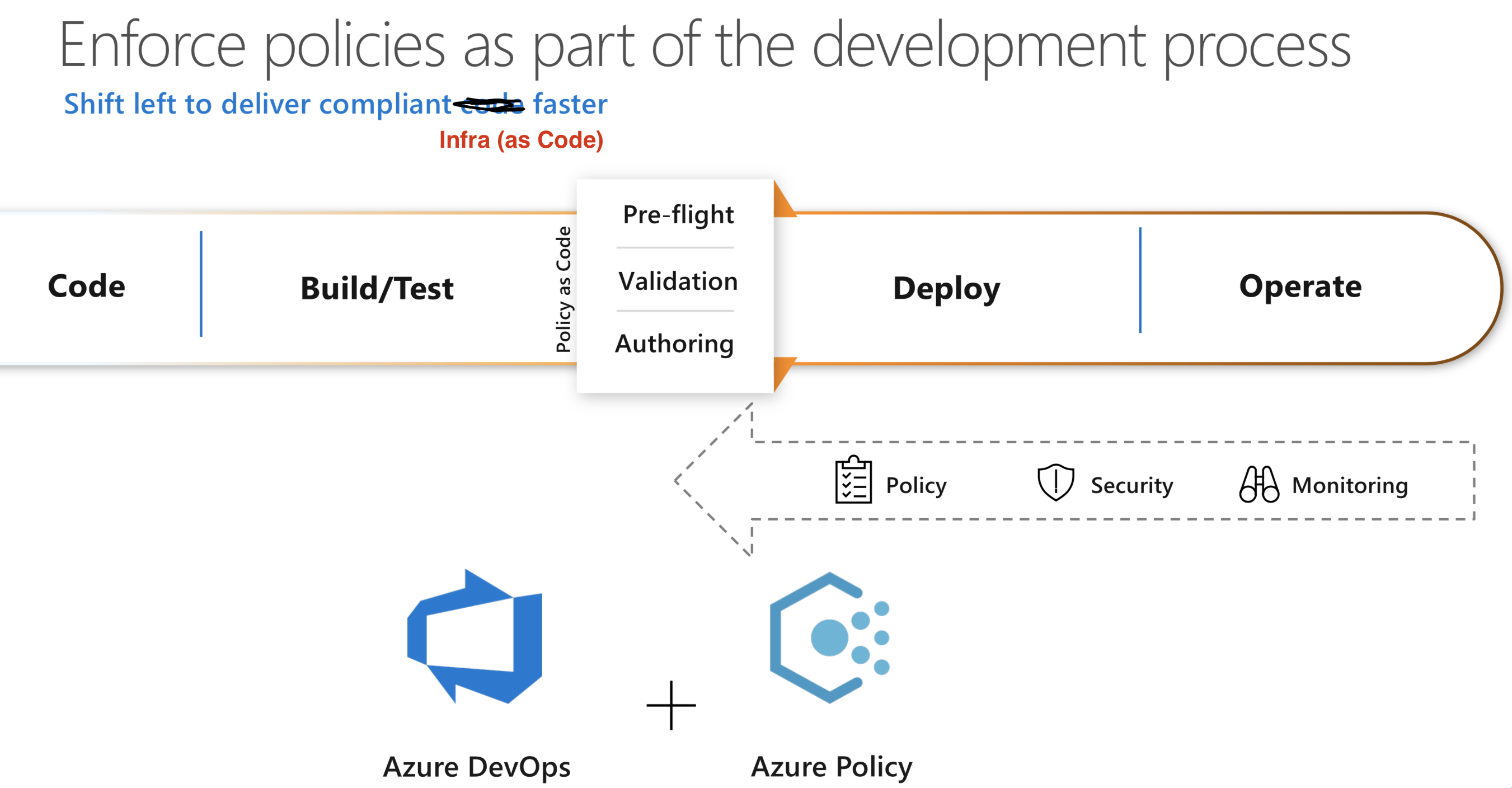
If you want to have a look at all of that in action, check at:
Azure Scaffolding
We used to talk a lot of “scaffolding” as it is an excellent checklist, or set of mandatory technical implentation details for a good cloud deployment. It is being replaced by the “landing zone” construct (see next section).
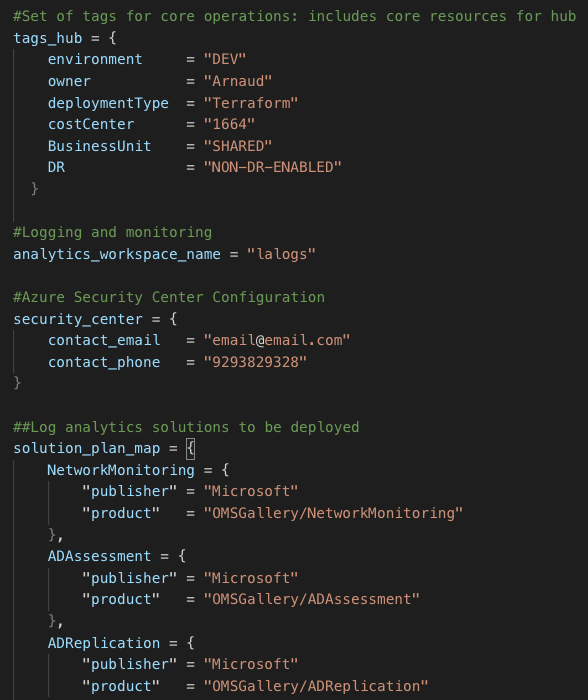
Here is a refresher picture about what scaffolding includes:
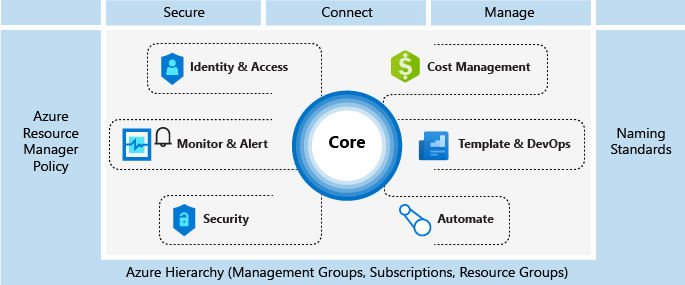
Important readings on Azure Scaffolding:
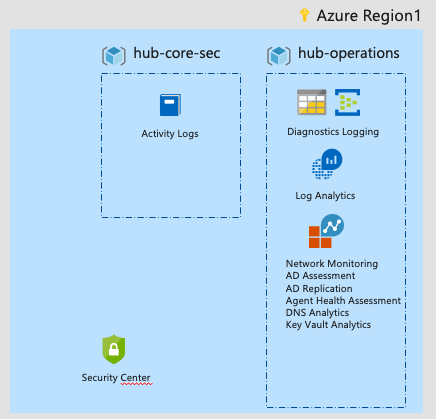
Azure Landing Zones
Landing Zone is our new construct to describe a good deployment, its replacing the scaffolding idea but takes all of its good ideas.
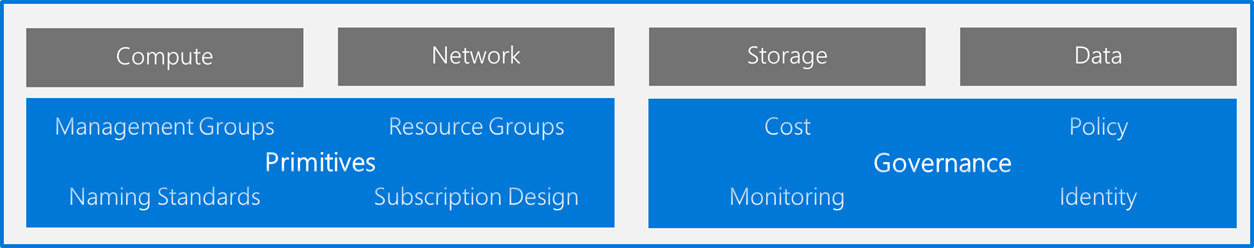
It has the idea of primitives which includes all mandatory decisions:
- Management Groups
- Resource Groups
- Naming Standards
- Number of subscriptions
On the technical implementations of Governance it includes all of:
- Policies
- Cost
- Monitoring
- Identity
Moreover, it comes with all set of decision trees in order to help you when it comes to implementation with your customers/partners:
Azure Virtual Datacenter
Azure VDC is a set of concepts, implentation guidance and automation scripts that allows you to build a highly available and highly secure datacenter, based on Microsoft Azure services.
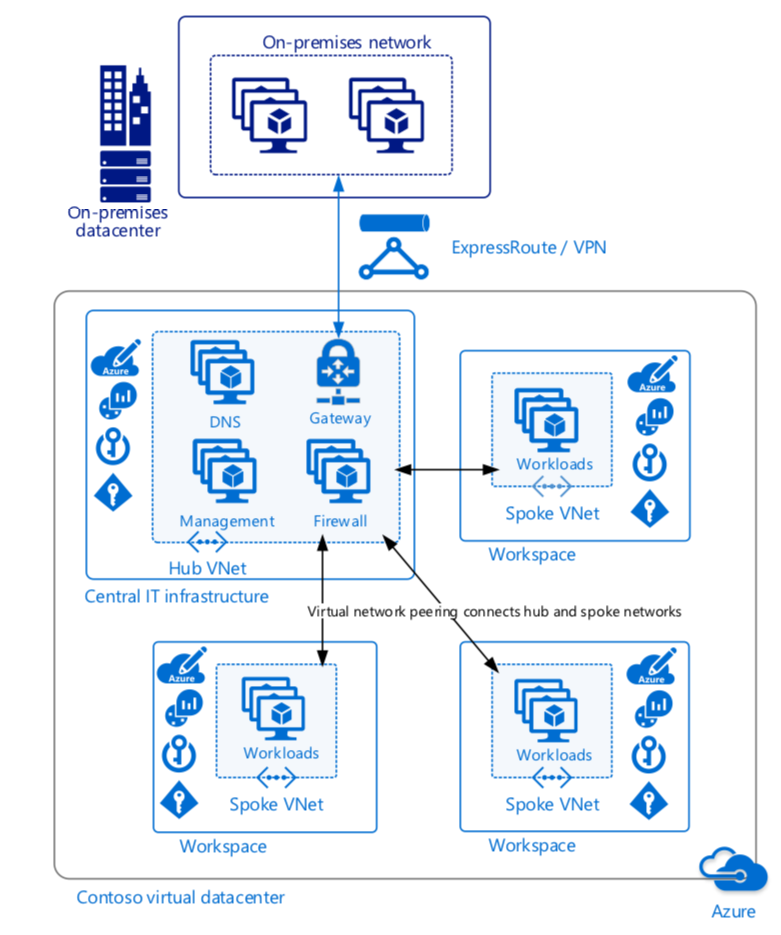
You can find all the materials here: https://docs.microsoft.com/en-gb/azure/architecture/vdc/
Check at the automation scripts and all the archetypes that allow you to deploy a VDC environment fast – based on Docker and Python : https://github.com/Azure/vdc
As last reference, as usual, our Azure Architecture Center
That’s it, now you will have a very well architected Azure deployment!
Arnaud